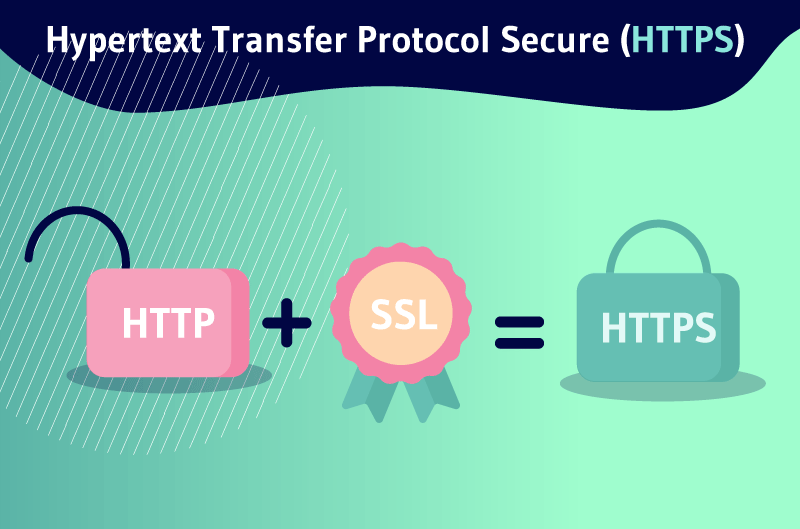
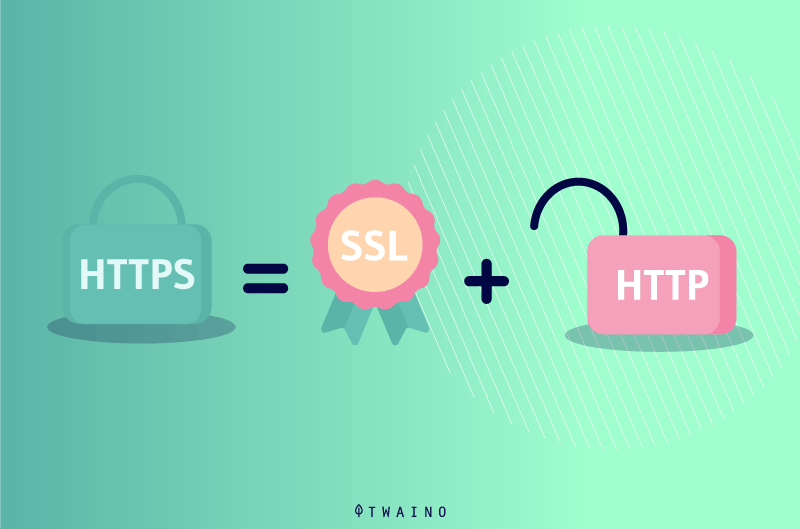
Hyper Text Transfer Protocol Secure or simply HTTPS, is a highly advanced and secure version of HTTP. It is the application protocol through which all data communications on the Web occur securely
Since 2014hTTPS encryption has become one of the ranking factors of Google and Chrome has marked all HTTP websites as insecure since July 2018
Now, other engines such as Mozilla, Safari and even Microsoft Edge have followed suit. This implies that every time you access a non-HTTPS website via one of the popular browsers, you get the corresponding warning.
This is one of the main reasons why you should definitely read this article to learn more about what HTTPS protocol is and how to switch from HTTP to HTTPS.
Chapter 1: What is HTTPS?
To better understand the concept of HTTPS will be the first objective of this article. To do so, we will address the following essential points
1.1) What is the history of the HTTPS protocol?
The HTTP protocol is the basic communication protocol that clients and servers must implement to ensure communication
Work on the protocol, as well as on the hypertext markup language (HTML), began in 1989 by Sir Tim Berners-Lee and his team at CERN.

Source fun-mooc
The first official version of the protocol (HTTP 1.0) was released in 1996, followed shortly by the currently widely adopted version (HTTP 1.1) in 1997.
The HTTP protocol transfers information between the browser and the server in clear text, allowing the network, through which the information passes, to see the transmitted data
However, there is a problem with the security of the data online. This is where HTTPS was introduced, allowing the client and the server:
- To first establish an encrypted communication channel,
- Then to pass HTTP messages in clear text through it,
- Then to effectively protect them against eavesdropping.
The encrypted channel is created using the Transport Layer Security (TLS) protocol, which was previously called Secure Socket Layer (SSL)
Thus, around 1996 and 1997, we got the current stable version of Internet HTTP 1.1, with or without SSL and TLS, which still powers the majority of websites today
Previously, HTTP was used for non-sensitive traffic, for example, reading the news. And HTTPS was used for sensitive traffic like: Authentication and e-commerce.
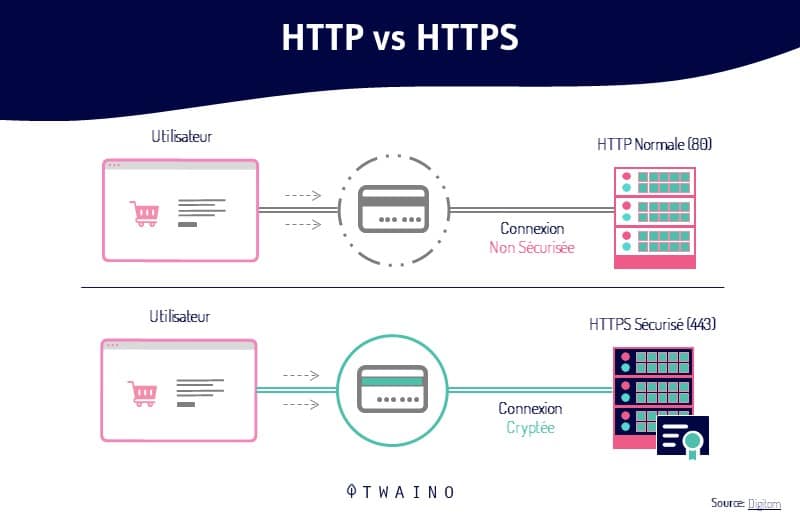
However, increased attention to privacy means that web browsers such as Google Chrome now mark HTTP websites as non-private and will introduce warnings for HTTP in the future.
The next update to the HTTP protocol – HTTP/2, which is being adopted by a growing number of websites, adds new features to reduce latency and increase performance and security.
In the HTTP 1.1 version, the secure connection is optional. You can have HTTP and / or HTTPS independent of each other. While in HTTP/2 it is practically mandatory even though the standard defines HTTP/2 with or without TLS, most browsers have stated that they will only implement support for HTTP/2 over TLS.
1.2 How does HTTPS work?
When looking at HTTP and HTTPS, it is important to note that HTTPS uses an encryption protocol that works on the original communication so that it becomes encrypted, i.e. secure.
The Transport Layer Security (TLS) protocol, secures communications using an asymmetric public key infrastructure, which is a combination of a public key and a private key.
The private key is managed by the website owner and remains private like a password. It resides on a web server and its role is to decrypt the information that the public network key has encrypted.
The public key can be obtained by anyone who wants to exchange data with the server in a secure manner. Once the information is encrypted by the public key, only the private key can be used to decrypt it.
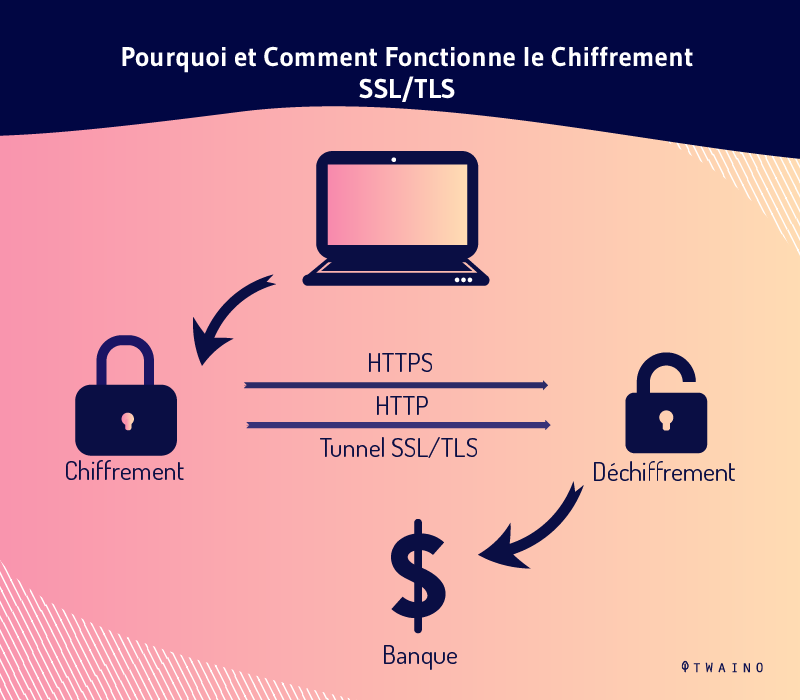
When a user connects to a Web page, the page sends the user its Secure Sockets Layer (SSL) certificate. This implies the presence of the public key needed to start a secure session
The client and server, interacting with each other, undergo a process called SSL or TLS handshake
This consists of several communications that ensure the security of the connection that now links the user to the server
Here are three key layers of protection that Transport Layer Security (TLS) and Secure Sockets Layer (SSL) offer users:
- Encryption
Because HTTP was originally designed to be a transparent, unencrypted protocol, it is easy for a bad actor to eavesdrop on connections and perform man-in-the-middle (MITM) attacks.
With SSL or TLS encryption, HTTPS can prevent data from being intercepted by anyone other than the client or server.
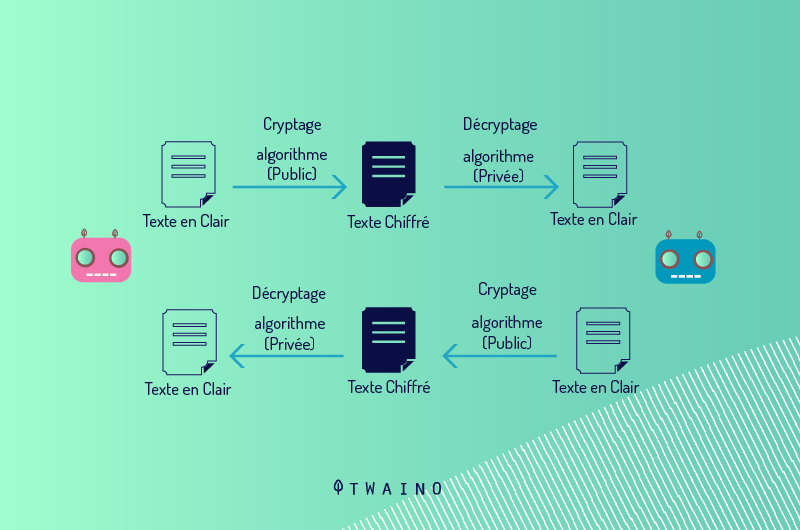
Using SSL / TLS binding and public key, communication occurring in an encrypted session can be established between the client and server using a secret key.
- Authentication
The SSL or TLS certificate of a Web site has a public key, which is used by the Web browser to ensure that what is sent from the server has a digital signature with the appropriate private key
Once the certificate is signed by a person authorized to authorize the certification of a server, the browser will assume that the credentials tracked in that certificate are undoubtedly validated.
- Data integrity
When you send a document to a browser using an HTTPS server, it has a digital signature that the browser uses to indicate whether it has been altered by a third party or corrupted in some other way
The server generates a cryptographic hash of the document content. This is included with the digital certificate. The browser can then resolve this hash, proving that the document is authentic and unchanged.
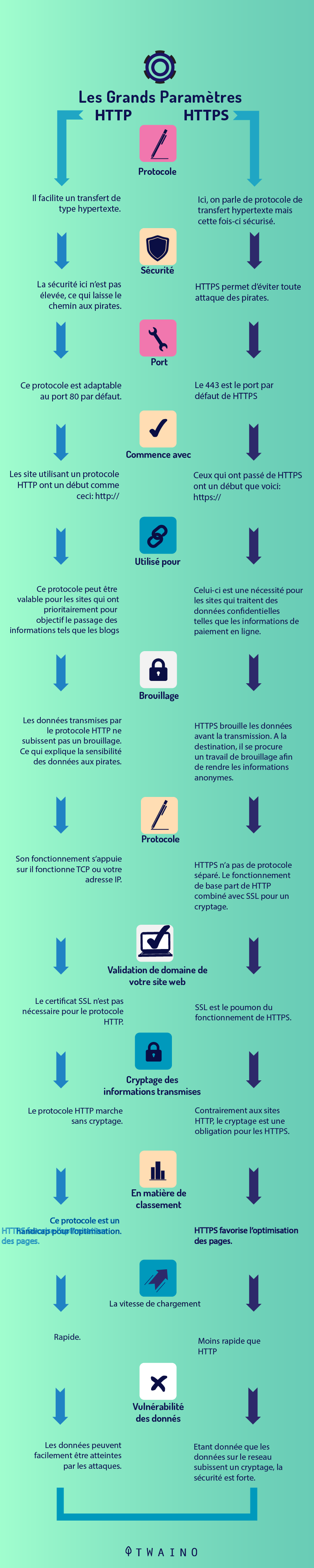
1.how are HTTP and HTTPS different?
HTTP and HTTPS help Web users transfer and receive information over the Internet. The most notable difference between these two protocols is the use of TLS or SSL by the HTTPS protocol.
However, HTTPS, with its secure transfer of information, is especially important for sites that often handle sensitive information
This is especially true for e-commerce sites where users submit payment information such as
- Billing addresses,
- Phone numbers,
- Credit card information,
- Etc,
HTTPS works with the TLS or Secure Sockets Layer SSL protocol to encrypt sensitive data, prevent data corruption or alteration during transfer, and authenticate certain users to communicate with the website.
Essentially, HTTPS provides security by generating short-term session keys for data transfers between a user and the website server.
We can summarize the difference as follows:
1.4. What are the SEO benefits of HTTPS?
In addition to providing a secure online experience for website visitors, adopting HTTPS has several SEO benefits:
1.4.1. Boost your ranking
Google now recommends that all websites use HTTPS connections as opposed to standard HTTP. By 2014the search engine giant announced that its algorithm would now consider HTTPS a positive ranking signal.
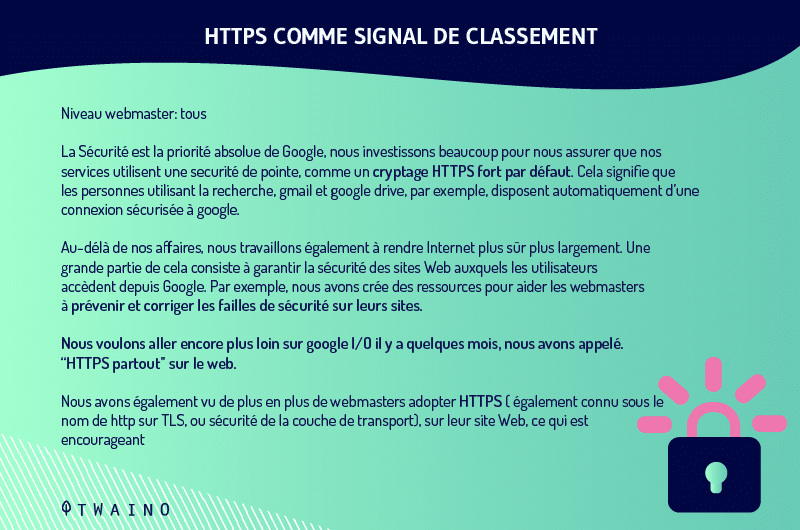
However, like most ranking signals, the influence of HTTPS alone is likely to remain fairly small
It is important to consider all ranking signals collectively in order to significantly improve rankings.
1.4.2. Improve the accuracy of the benchmark data
When you switch from HTTPS to HTTP, you automatically lose your baseline data that you will later find in your Analytics report as direct traffic. This is problematic in that it leaves you with inaccurate traffic data.
With the opposite scenario you switch to HTTPS, whether the original site is secure or not, the referral information is retained and will appear in Analytics accurately.
1.5. What are the challenges of HTTPS?
For all the benefits of switching to HTTPS, it is also important to consider the potential implications involved:
- Page load speed
Because HTTPS requires more communication between servers, page load speeds can be slowed
Not only is this an issue for the user experience, but page load speed is actually a Google ranking factor.
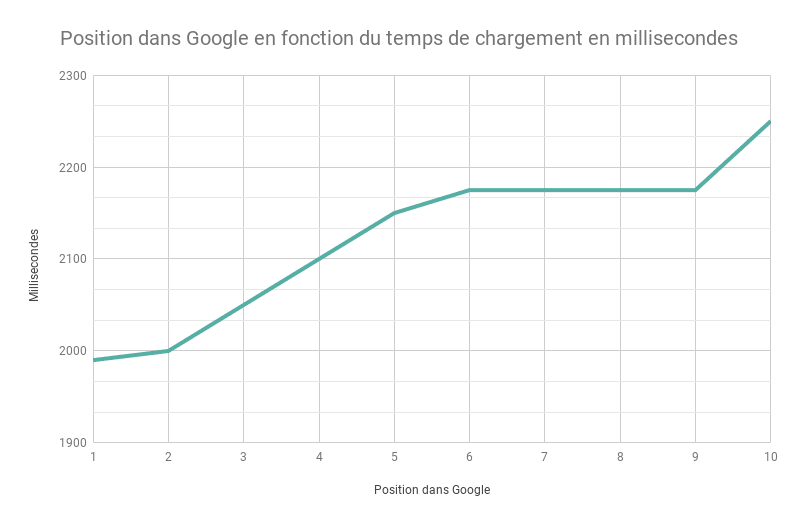
However, there are a number of things your SEO agency can do to reduce page load speed to mitigate the effects.
- Ranking fluctuations during site migration
Google treats a migration from HTTP to HTTPS as a site move with a URL change
As a result, you may experience fluctuations in rankings while Google re-explores and re-indexes the site.
1.6. Types of HTTPS certificates
There are several types of HTTPS certificates that we will classify as follows
1.6.1. According to the identity validation
Domain validated DV this is the most common type of certificate. A DV certificate verifies that the domain corresponds to a particular public key. A highly secure connection is established between the browser. This is symbolized by a closed padlock in your browser
When you click on the sign to view a message like “This website does not provide ownership information” will be presented to you. A DV certificate simply guarantees that it is the correct public key for that domain.
EV Extended Validation Certificates certificates: They verify the legal organization behind a website. This is the most trusted type of certificate, obtained after a certificate authority has verified the legal entity that controls the domain
The legal entity is verified with a combination of :
- Domain control as a DV certificate,
- Government business records, to ensure that the business is registered and active.
Validated Organization (OV) like EV, OV certificates verify the legal organization behind a website. However, unlike EVs, HTTPS OV certificates do not display the verified legal name in the user interface
As a result, OV certificates are less popular, as they have high validation requirements without sufficient benefits to users
1.6.2. Depending on the number of domains covered
In the past, HTTPS certificates usually contained a single domain in the CN field. Later, the alternative subject name (ASN) field was added to allow additional domains to be covered by a single certificate
Nowadays, all HTTPS certificates are designed in the same way. Even a single domain certificate will have one SAN for that single domain and a second SAN for the wwwversion of that domain
However, many certificate providers still sell single and multi-domain HTTPS certificates for historical reasons.
Single domain this is the most common type of certificate, valid for example.com and www.example.com.
Multiple domains (UCC / SAN) multiple Domain (UCC / SAN): This type of certificate, also known as a Unified Communications Certificate (UCC) or Subject Alternative Names (SAN) certificate, can cover a list of domains up to a certain limit
It is advisable to use it with related websites, as a client inspecting the certificate for one of the websites will see the main domain, as well as all the others.
Chapter 2: Tips for switching from HTTP to HTTPS?
Switching from HTTP to HTTPS may seem a bit complex, so I suggest you follow the 5 steps below:
Step 1. Choose an SSL certificate
To enable your website to establish an encrypted connection, you must first obtain a TLS certificate, better known as an SSL certificate
The thing is, after a major upgrade, the certificate was renamed to TLS, but the old name remained. The certificate is a small file that contains an encryption key as well as verified information about the website owner
Depending on the amount of data you provide about the person or company that owns a website, you can get one of three types of certificates.
Step 2: Obtain and install an SSL certificate
Option 1: Purchase from your hosting provider
Once you’ve decided what type of SSL certificate you need, check out what your hosting provider has to offer. If the price is reasonable, this would be your best choice as you will get things done faster and easier
The standard procedure for obtaining and installing an SSL certificate is as follows
- You choose the type of certificate that suits you best,
- You generate a private encryption key and a certificate signing request (CSR) from your hosting provider,
- Order an SSL certificate from the selected provider. At this point, you will need to upload the CSR file you generated earlier,
- Once the certificate signing request is submitted, you will need to go through the verification process which will vary depending on the type of certificate (DV, OV, EV),
- Once the validation is complete, you will be able to download your SSL certificate from your provider’s website and upload it to your hosting server.
As you can see, things get a little complicated, as you have to get files from a hosting provider, then upload them to an SSL certificate provider, and vice versa
If you purchase an SSL certificate directly from your hosting service, there would be no need for such file exchanges and you should be able to cross a few things off the list.
In any case, contact your hosting provider to find out how they can help you switch to HTTPS. Also, check to see if by chance your hosting plan includes a free SSL certificate. Some providers offer such a benefit
Option 2: Buy from the Certificate Authority or a specialty store
If, for some reason, you can’t get an SSL certificate from your hosting provider, there is an option to buy one directly from a company that issues such certificates (Comodo, Symantec, Geotrust).
Option 3: Get it for free
Thanks to the Let’s Encryptinitiative, there is also an option to get an SSL certificate absolutely free
The certificates they issue work in the same way as paid certificates with only one difference: They are only valid for three months while normal SSL certificates last for one year
Therefore, you will have to constantly renew your Let’s Encrypt certificate. In addition, they only provide DV certification

After installing the SSL, you will have to make sure that it works properly. You can use SSL Server Test for this purpose
It will check if the certificate is valid, what encryption protocol is used, the strength of the encryption and calculate the overall score of your website. The highest possible score is A+, and if you get a lower grade, the service will show you why.
Step 3: Force using HTTPS
Once your SSL certificate is successfully installed, your website will become accessible via both HTTP and HTTPS. The problem arises with search engines, as these are two separate websites that can compete in the SERP
To facilitate access to your site via HTTPS from now on, you will have to set up a redirect.
Over time, as your website’s HTTPS pages are indexed, their HTTP version will disappear from the SERPs and the link juice will shift to the HTTPS version of your website
Now, there is one thing you need to do before setting up redirects: Replace all absolute URLs on your website with relative URLs
E 3.1 Implementing relative URLs
First, let’s define what relative and absolute URLs are
An absolute URL contains the complete address of a page, including the connection protocol and domain name. Most URLs you see on the Internet are absolute, for example https://twaino.com/blog/
Relative URLs, on the other hand, are used for internal links. They do not specify the connection protocol and may or may not contain the domain name, for example Twaino.com/blog/ or simply / blog
If a website uses relative links, the browser itself adds the missing protocol and domain name to the web page address
It assumes that a relative HTTPS link on a web page must point to another page on the same website that also runs on HTTPS
You will need to replace all of the following absolute links with relative links: Internal links, paths to stylesheet, scripts, images, video
Otherwise, you will notice duplicate content on your site. This happens when some page elements load via the secure HTTPS connection and others via the insecure HTTP protocol.
These web pages are vulnerable to man-in-the-middle attacks because the elements that load via HTTP allow hackers to take control of the entire page
Naturally, browsers mark pages with duplicate content as insecure. You need to be very sure that all resources on your website load via HTTPS
So you can spend hours fixing internal links and rewriting file paths to images, videos, scripts, etc. after enabling redirection.
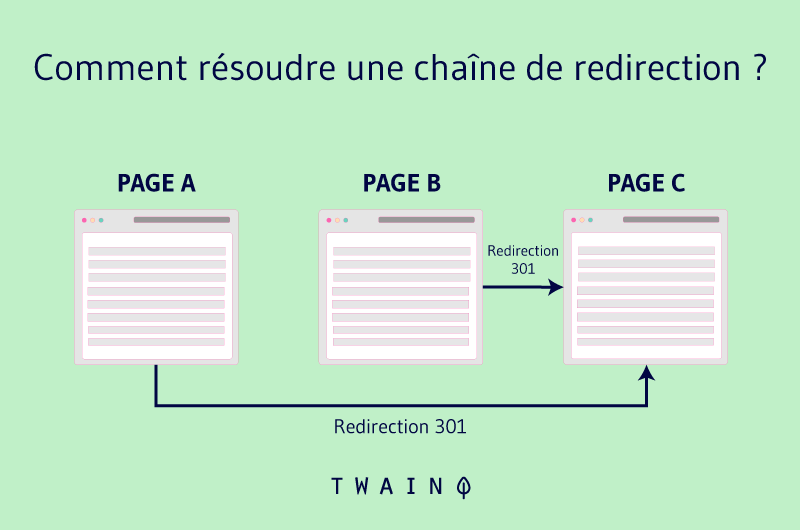
E 3.2. Configure 301 redirects
To redirect users and search bots to your HTTPS website, use server-side 301 redirection. It tells browsers that the page is definitely transferred to a different address than the old one
The configuration is often not the same for different types of web servers. If your site is hosted on a server running Apache, it will be even easier to add a certain line of code to your .htaccess file

You can find the file in the root folder of your website, but keep in mind that it may be hidden. In this case, you will have to go to the settings of the administration panel and check the box ”Show hidden file”
Be sure to copy the file before editing it to have a backup in case of problems. If you have not located the file, it means that your website does not have one and you will have to create it yourself using a standard text editor.
Step 4: Update your Search Console
Even after setting up the redirect, your HTTP pages will still be ranked on Google. To get them replaced with HTTPS versions, they need to be crawled and indexed
You can speed up the process by importing an updated version of your XML sitemap into Google Search Console. Before that, you may need to add your HTTPS website to GSC
The fact is that in February 2019, Google launched Domain Properties to allow webmasters to analyze domain data
Domain property is a URL without protocol (HTTP / HTTPS), www prefix or other subdomains ( support, help, etc)
So if you add yoursite.com to GSC, you will get combined data on different versions of your website address, including
- yoursite.com,
- www.yoursite.com,
- m.yoursite.com,
- www.m.yoursite.com,
- help. yoursite.com,
- yoursite.com.es
And dozens of other possible variants with both HTTP and HTTPS protocols. The only way to create a domain property is to go through the DNS record check
Now, if you’ve set up a domain property in your GSC, it will automatically start collecting data on HTTPS URLs
But if your website has a URL prefix ownership status, you will need to manually add the HTTPS variant of your website
Again, you have the choice of adding it as a URL prefix property or checking your property via DNS and creating a domain property to see the aggregated data.
Step 5: Find and fix errors
Since we implemented relative URLs on the website before forcing HTTPS, no critical technical errors should occur after configuring the redirects. Nevertheless, a good practice would be to perform a website audit and make sure everything is working properly
Pay attention to the following issues
- Existing pages should return the 200, nonexistent 404 status code,
- HTTPS pages should not be blocked by a robots.txt file or a noindex meta tag. Otherwise, Google will not be able to explore and index them,
- The rel = canonical and rel = Alternate tags, as well as the hreflang attribute, must point to HTTPS pages,
- Pages must not return mixed content errors, which means that every page element must load via HTTPS protocol.
You can easily detect all these problems, you need to perform a full audit of your website.
Conclusion
Switching to HTTPS may seem like a very daunting task. But you must remember that your ranking and traffic are at stake
You should not allow yourself to stick to HTTP, as you will compromise the security of your users and lose their trust
To avoid all this, we have leveraged our knowledge to bring you everything you need to know about HTTPS